Shadow Identity, how to fix internet identity
Intro
Identity lies at the heart of any network, with the Internet being the most expansive network we know. Each node connected online essentially represents an identity, whether an IP, MAC, email address or someone’s laptop. This underscores just how crucial the concept of identity is on the internet. However, there are problems we have yet to crack.
Have you ever wondered - why there is no online voting mechanism yet?
I've built more than 30 mobile social apps, and my YC-backed startup grappled with users registering new numbers, making purchases, and then asking for Stripe refunds - a strategy I learned is a typical money laundering method using stolen credit cards. As it turned out, resolving this wasn't straightforward without compromising UX.
This issue of fraud led me to delve into the question, "Why is this still happening?". The answer appears to be the same as for the voting issue – “internet identity is broken.”
This article is solely my own opinion, introducing a potential solution as a concept on how to fix identity and is condensing into three sections: Why? (The problem); What? (The solution); Now what? (Use cases).
Why?
Digital identity issues today: 1) No ownership of data and identity; 2) poor UX for reusing the data, authenticating, and registering; 3) fragmentation with hundreds of accounts and new KYC checks; 4) no privacy; 5) no trust; 6) Sybil attacks; and 7) AI concerns.
The first three are clear, but there are a few things about the others:
One more word about ownership. To rectify the identity concept, which should have been an integral part of the Internet protocol, it needs to be as neutral as possible and collectively owned — each identity owner retains ownership of their identity, and the entire system is held in trust by humanity. This is important because if the concept of identity becomes the property of a centralized body/ies, it's relatively equivalent to the Internet being owned by a centralized entity (which we're already seeing with google/facebook, but it will become much worse).
No privacy. Recently I needed to obtain a UAE ID. During the process, I was required to send my passport picture to a government agent via WhatsApp.
There’s no ability to validate my data without exposing it and proving I'm 18+ or born in the US. I can't selectively share my data (say, just my address without other personal details). I can't maintain anonymity when I desire and certainly have no visibility into where my data is used after I've shared it with a KYC provider.
In some countries, messenger conversations can be read since the services you use are subject to their jurisdiction. And the issue is not a lack of encryption.
No trust. How can one ascertain that @alice on Twitter and @alice on Instagram are the same person, especially if they lack a consistent, identifiable profile or photo?
How can one determine whether or not to trust a virtual contact, regardless of the context or reason for the interaction? And how can I know that you are who you claim to be and you’re real?
Lack of Sybil resistance. The concept of Sybil resistance, at first glance, is about cheaply creating fake identities to trick a reputation system. But there's more.
While Proof-of-Work (PoW) predates Bitcoin (PoW was first conceived in 1993), Bitcoin’s true innovation resides in its solution to the double spending problem. PoW is effectively addressing Sybil resistance by establishing an "identity" within an anonymous, decentralized ledger using "costly" computations.
However, PoW is just a proxy and not a scalable solution for decentralized identity. The ideal would be to mark an online entity as a unique, real human and the ability to check if they actually represent who they claim they are, additionally allowing any developer to utilize it with an identity persistent reputation.
When this topic arises, many people express fear of online surveillance – “I don’t want someone to spy on me if I have a unique non-changeable ID!”. But having a unique online form doesn't necessarily negate the possibility of maintaining anonymity or privacy if desired.
AI Concerns. Distinguishing between a human and an AI is an ever-growing issue of AI Safety, and the current only practice of “good AI” for finding “bad AI” is an addition, not a solution to the problem.
What?
There are commonly confused two separate concepts about new identity solutions. The first revolves around personal data ownership and the option for privacy, also known as self-sovereign identity (SSI). The second deals with the uniqueness of identity and confirming the existence of a real person behind it.
SSI, by default, means decentralization, so all following mentions of SSI would mean that the identity is being stored on the blockchain.
The purpose is to lay out a fundamental framework that enables translating anyone’s online persona and every aspect of their identity.
Here are a few things we should agree on:
1. Let's accept that identity stems from an owner. This owner, an "entity," could be a human, another identity, or possibly an AI in the future. Can ownership be transferred? Depends on the use case, but in the context of humans, my initial inclination is no. Another question is the ability to prove ownership to others in a trustless way.
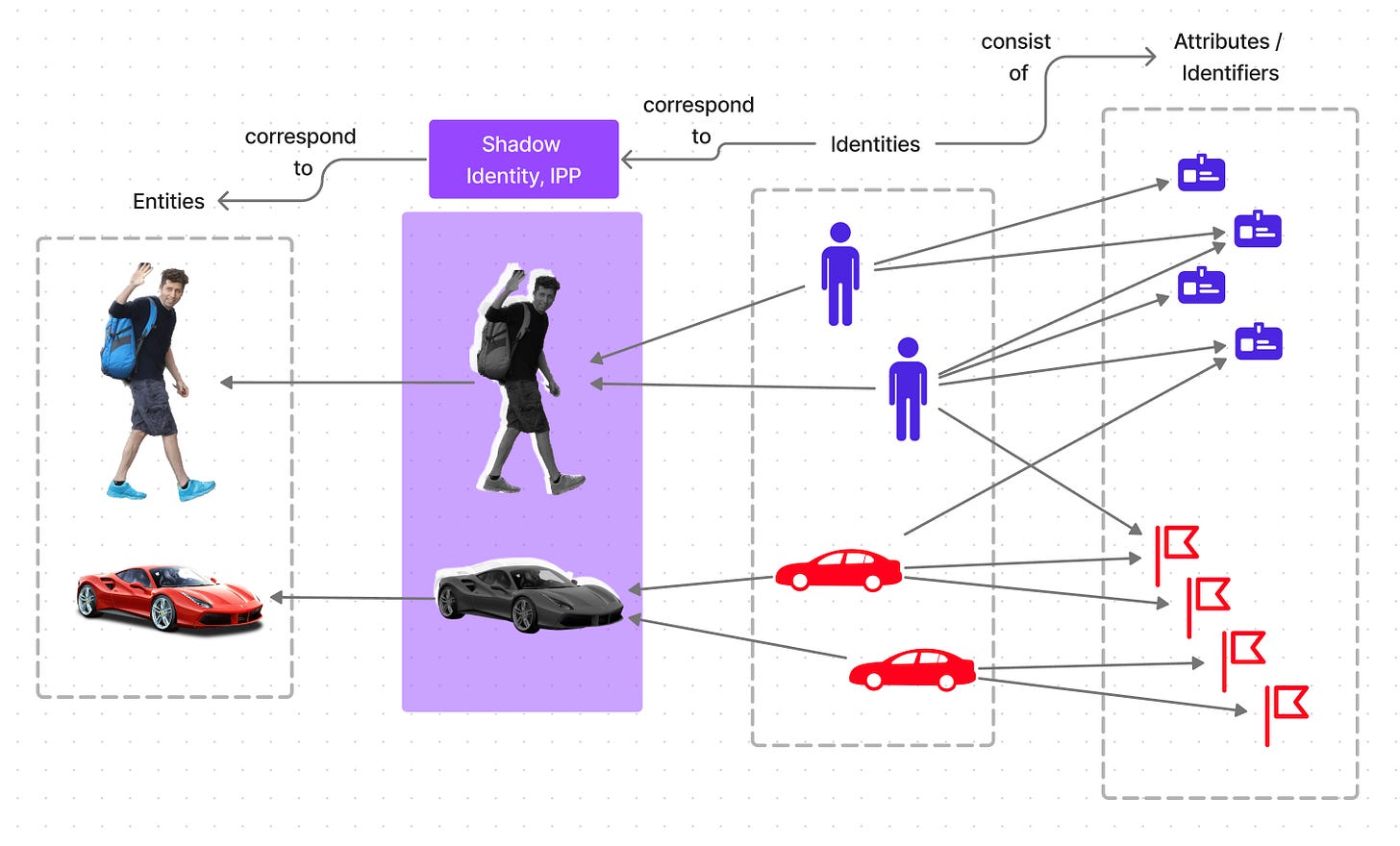
2. Entity can have a near-infinite number of identities. Identities can tie to other identities and have a near-infinite number of subidentities.
3. Identity can have a near-infinite number of attributes. Each identity is linked with certain associated elements, whether they're connections to other identities, data, or basic features like gender, URL, or eye color. This implies that each identity should also have some form of "storage" tied to it.
Shadow Identity
Let’s introduce two concepts for further explanations: "Identity Primary Proxy" (IPP) or “Shadow Identity” and "Identity Proxy" (IP).
An Identity Proxy (IP) is an identity that serves as a wrapper or a mediator between one identity or an entity (a human being) and any other one or multiple identities. The main feature of IP is retaining ownership of one or multiple identities, becoming a singular access point. Account abstraction on Ethereum could be counted as a specific implementation of IP.
On the other hand, a “Shadow Identity” or Identity Primary Proxy (IPP) is a specific implementation of an IP. Shadow Identity is a Sybil resistant and self-sovereign IP linked to a level-0 entity (a human being). It also addresses the issues of proof-of-personhood, proof-of-ownership, and proof-of-identity.
Ideally, every individual should possess only one privacy-preserving Shadow Identity that acts as the primary access point to ALL of their identities, including the centralized ones we currently use, like a Twitter profile.
This Shadow Identity concept is somewhat different from the one suggested by crypto enthusiasts who propose that any Attribute of identity could be represented as a soulbound token, and a proof-of-personhood token could potentially solve Sybil attacks. While both solutions may be feasible, I believe the soulbound approach could serve as an addition to Shadow Identity. This is because soulbounds alone can't tackle the challenges related to onboarding, UX interoperability, and bridging on-chain with existing internet.
This model doesn't hinder the creation of multiple identities; rather, it facilitates the establishment of a global ID system owned by individuals in a privacy-preserving manner and serves as a mediator (IP) to all of the existing right now and future identities.
1. Self-sovereignty (SSI)
It addresses questions of ownership, trust, and interoperability. The principle is that an individual has exclusive ownership over their identity and its associated data. I believe SSI must potentially be based on a trust model superior to a 1 of 1 (centralized system). The closest examples we currently have are wallet addresses on the blockchain. These wallets essentially act as an identity, taking responsibility for the data, not just the assets. While they're transferable and may not solve the problem of Sybil resistance, they offer a level of self-sovereignty that's far more robust than existing systems.
2. Privacy
Privacy is the current issue of existing blockchains. With SSI, you maintain control over the level of anonymity or public exposure you want since an individual fully keeps the ownership. All associated data and Attributes are private by default and can be selectively shared, verified, and proven through verifiable credentials. The catch, however, lies in the UX. If I choose to make my profile picture private, it's an all-or-nothing scenario - I can either make it private for everyone or public for all. Attempting to make it partially private could inadvertently lead to data centralization.
3. Sybil resistance
Sybil attacks remain an unresolved issue in a decentralized setting. As previously discussed, there are many interim solutions like the PoW system, which, while innovative, lacks scalability and practicality for regular use as an identity provider.
In the identity paradigm, we should divide Sybil resistance into three layers: Proof-of-Personhood (PoP), Proof-of-Ownership (PoO), and Proof-of-Identity (PoI).
Proof-of-Personhood (PoP) — an individual is a real, unique human being. It’s possible to divide it even more — Proof-of-Realness and Proof-of-Uniqueness. It's a neutral concept that doesn't require knowledge of someone’s personal data - it’s an attribute attached to the identity.
Proof-of-Ownership (PoO) — Does an individual truly own and use their identity or not.
Finally, Proof-of-Identity (PoI) resolves the question of "who you are". It is worth remembering that someone could hold multiple legal identities, which is why PoI can't single-handedly tackle Sybil attacks.
If properly implemented, these three layers enable to navigate Sybil resistance online. PoP and PoO are particularly crucial in anonymous networks like Bitcoin, but for daily use in real life and to address the fourth point of interoperability, PoI is necessary.
The mechanism has to have these characteristics:
The mechanism should be as inclusive and egalitarian as possible.
The data can be provably provided to crypto-economic systems (e.g., blockchains, smart contracts).
The cost of obtaining one identity should be as low as possible and as high as possible for multiple identities.
The cost of obtaining multiple identities in an automated system should be as high as possible.
Preventing identity theft by prohibiting adding people without their knowledge.
Temporary and permanent transfer of control over their identity from one user to another should be economically disadvantageous.
Users’ personal data should be transmitted, stored, and reviewed securely, ensuring privacy. Access to this data should require direct permission from the data owner.
There shouldn't be a single trusted authority (governments or companies) in charge of issuing identities, as they could manipulate the system.
4. UX interoperability
Decentralization comes with its own set of challenges. While privacy, Sybil resistance, and self-sovereignty combine to form the concept of Shadow Identity, there are still questions to answer:
How to handle private keys ensuring minimal security risks and reducing centralization while improving the UX compared to what crypto has now?
How to be user-friendly and easily understandable for my mom, minimizing technical complexity for super low friction onboarding and consequent usage? Or, how to onboard humanity into the Shadow Identity solution?
How can I connect my current centralized/decentralized identities without losing backward compatibility?
And finally, how should passwordless authentication function, or what should be a better solution than logins and passwords?
Concepts such as passkeys, account abstraction, homomorphic encryption, and social recovery are still not wholly refined but are promising. Although the Shadow Identity concept can smoothly integrate with the current digital landscape, the primary challenge lies in the onboarding and identity management processes.
Another crucial point to remember is the inclusiveness of all individuals, regardless of age, country, or race.
Questions
Now what?
While still having UX interoperability issues, Shadow Identity can solve problems like fragmentation, privacy, trust, and authentication. It could also unlock new use cases:
Democratic and other forms of digital voting — this cannot be built on centralized platforms like Twitter because of trust issues and must be Sybil resistant.
Wealth redistribution and taxation — public goods, quadratic funding, UBI
Network States & Governance — digital forms of communities with their own currencies, constitutionz, passports, etc.
Persistent reputation, reputation systems, credit scores — existing implementations for credit scores are far from ideal, but we can experiment and come up with something more practical than SSN.
Anonymous Polls, Petitions — no need to explain.
Incentivization programs, airdrops — games could give lots of perks knowing that the user is unique; any apps could come up with creative ways of distribution.
Bot protection and community moderation — having a bad reputation score or being able to be permanently kicked is the primary tool for moderation protection.
AI & Human — using proof of ownership, it can be possible to temporarily
Offline — everywhere where you’re asked for a physical ID, passport, or driver's license is a place with lots of friction, and Shadow Identity solves the trust issue.
More — some things are possible that we can’t even imagine. As smart contracts appeared as a new block with the whole industry of defi, we can expect lots of valuable things built for society.
Conclusion
Shadow ID system introduces a solution that could be a mediator to all existent identities but also be owned entirely by an individual and prove they are who they claim they are.
However, numerous challenges exist. Implementing this framework requires addressing inclusivity, ensuring low-cost and high security for individual identities, yet deterring multiple identity creation. A system must be resistant to manipulation by a single trusted authority. UX challenge lies in compatibility with existing systems for low friction onboarding.
I plan to write more about this topic and post it on Twitter.